SQL injections are a type of cybersecurity attack that targets the databases underlying a web application. In a SQL injection attack, malicious SQL code is inserted into input fields on a website, exploiting vulnerabilities in the website’s code that allow the attacker to execute arbitrary SQL commands.
The goal of a SQL injection attack is typically to gain unauthorized access to the database or to manipulate its contents. Attackers can use SQL injection to extract sensitive data, modify or delete data, or even take control of the entire database server.
In 2023, SQL Injection emerged as the primary source of critical vulnerabilities in web applications worldwide, accounting for 23%. Additionally, 19% of critical vulnerabilities in internet-facing applications stemmed from stored cross-site scripting attacks. Below are the statistics.

By Prabir Kundu, AVP, Pre Sales and Cloud & Platform Management Services, Path
Distribution of web application critical vulnerabilities worldwide as of 2023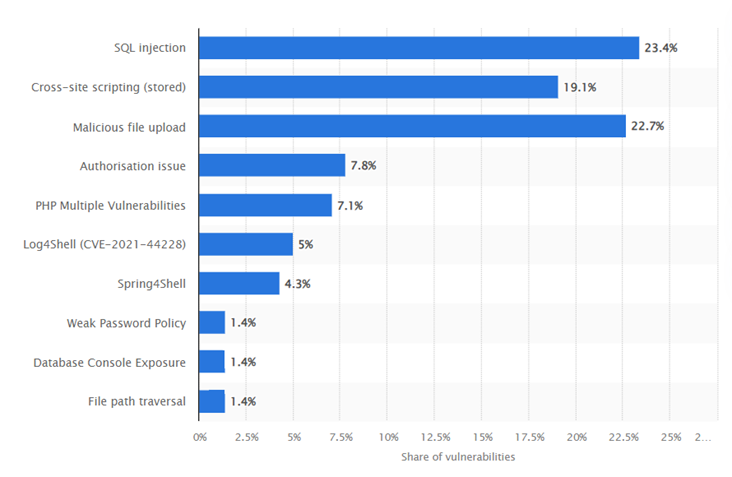
Source: Statista
Addressing SQL Injection and Compromised Accounts
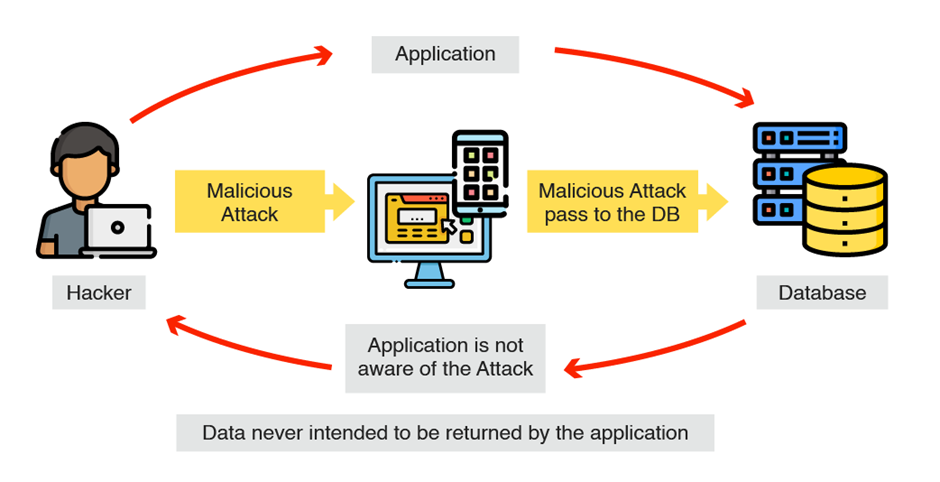
Ensuring robust security measures is essential for protecting your database against SQL Injection attacks and minimizing the threats posed by compromised accounts. These are the main ways hackers can get into your system.
While fixing application code and implementing a Web Application Firewall (WAF) are often touted as solutions to mitigate injection attacks, attackers can circumvent these measures using pattern-matching techniques. Consequently, these attacks remain difficult to prevent without addressing vulnerabilities within the databases themselves.
High-Level Problem
Solutions Available
To tackle the security issues mentioned above, Oracle has introduced a robust SQL Firewall directly into Oracle Database 23c. This integration effectively deals with SQL injection attacks and compromised account problems. It provides a straightforward solution with minimal impact on performance.
1. Application:
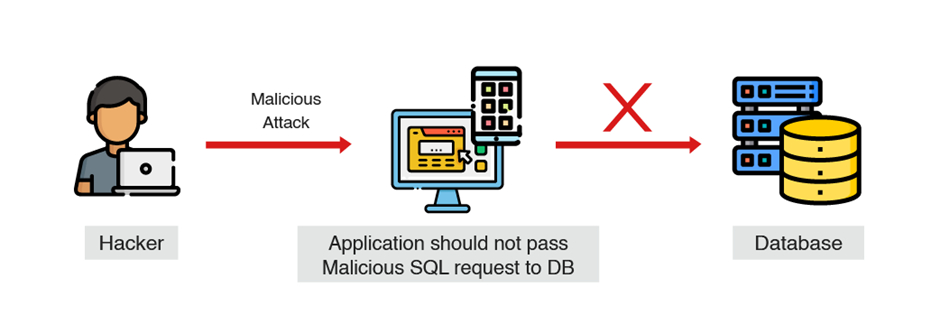
What it does: The application prevents this SQL from reaching the Database.
How it works: Conducts input validation, a well-established method with a lengthy history.
Limitations: Reliability is compromised due to developer errors, and configuration controls such as code reviews often overlook issues. Additionally, new vulnerabilities are continuously emerging.
2. Web Application Firewall (WAF):

What it does: WAF identifies SQL Injection attempts.
How it works: Many WAFs rely on signature pattern matching to detect and block known SQL injection payloads.
Limitations: Unable to defend against zero-day exploits. Typically, a WAF cannot analyze the content of the injection payload thoroughly or consider the complete SQL context when making decisions.
3. Database Firewall:
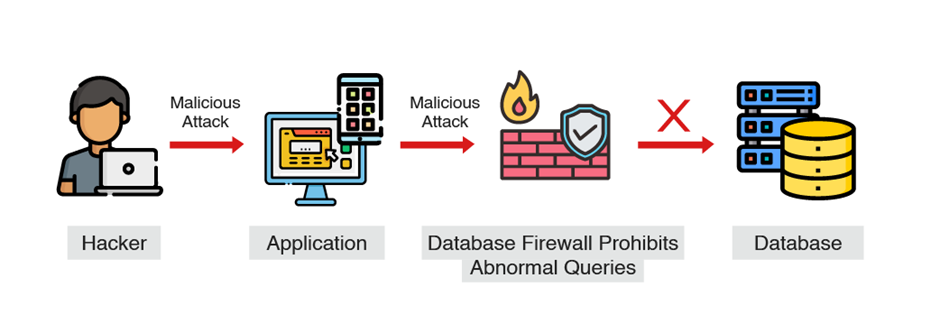
What it does: The Database Firewall comprehends typical application SQL and prohibits abnormal queries.
How it works: Operates based on an allow-list of authorized behaviors rather than signatures. It analyzes SQL statements to grasp their intent.
Oracle’s Advanced SQL Injection Prevention Techniques
Oracle’s answer to preventing SQL Injection is the Database Firewall, which scrutinizes the traffic directed toward the database before it gets processed. It employs two methods to shield the database from SQL Injection:
- Audit Vault and Database Firewall (AVDF) Network-Based Database Firewall.
- The Oracle SQL Firewall is integrated into the database kernel (a new feature in version 23c).
Unlike traditional application-based firewalls, neither of these methods relies on regular expressions or signature-based matches. Instead, the database firewall:
- Learned the typical SQL traffic patterns of applications.
- Alerts or rejects any SQL traffic that deviates from its learned model.
In conclusion, SQL injections are a major cybersecurity threat, targeting databases via malicious code in web applications. In 2023, they accounted for 23% of critical web vulnerabilities globally. Traditional defenses like code fixes and Web Application Firewalls (WAF) often fall short. Oracle Database 23c offers a robust solution with its integrated SQL Firewall, which effectively blocks abnormal SQL queries, providing strong protection against SQL injection attacks.
Disclaimer: The content presented in this blog post is sourced from Prabir Kundu’s original LinkedIn blog. To read the full blog click here.